Hello, this is IRISnoir from Hackingarise. Bringing to you another tutorial.
Today we will be discussing about one of the most essential steps in hacking: Scanning, and it’s representative, Nmap.
Now, hacking has 5 phases:
– Reconnaissance
– Scanning
– Gaining access
– Maintaining access
– Covering tracks
We will focus on the scanning phase.
Scanning refers to the technique used by hackers to uncover vulnerabilities in a system. Once a flaw is detected, the hacker can proceed to use it to their advantage to compromise a system.
Let’s take a real-life scenario as an example.
You are a burglar, and you wish to rob someone. But you need info about them and their security level. This is the part where you scan them. You look out for places that you can enter safely and quickly into and out of their house, also have an eye out for dogs, security cameras, etc.. In order not to alert the owner in any way as you break in.
DISCLAIMER: Don’t take this as advice for breaking and stealing as it is illegal and can land you in jail.
Now, you get the gist of how it works, we go to the tool and it’s usage.
Brief description of it’s usage:
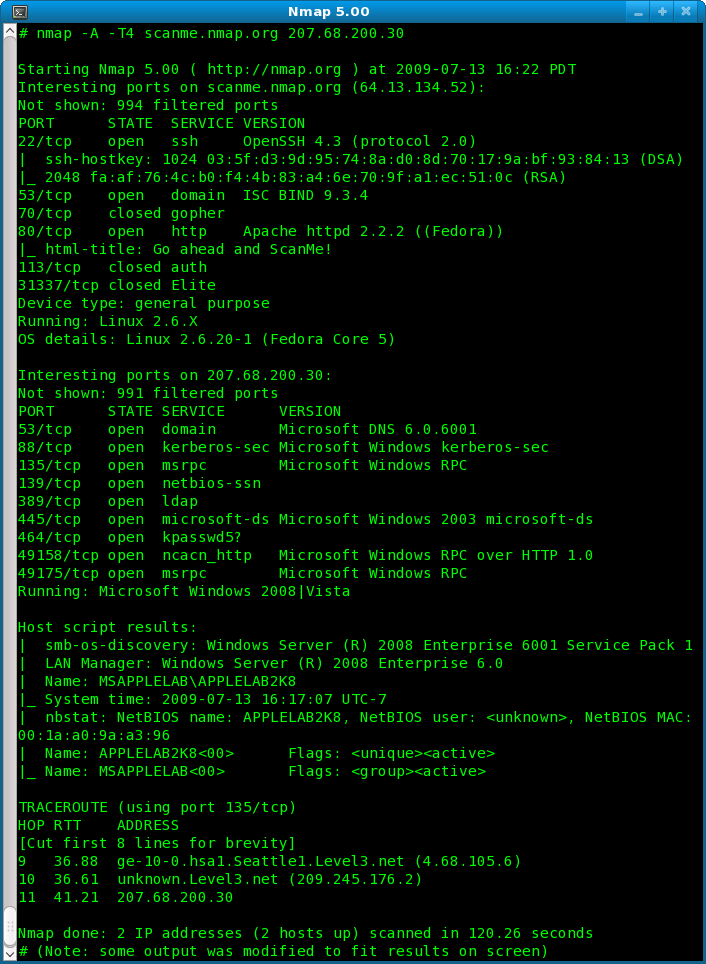
The tool’s name is Nmap, as you can see in the title. It is a network mapper which enables you to map your whole network or an IP or domain. This includes finding open ports, looking for vulnerabilities, scanning your network, etc..
Now you will want to open the help menu:nmap -h
Don’t worry, it’s not as hard as you would think. In fact, it’s really easy.
Let’s try to perform those network scans.
The network scan:
First you want to connect to your network by accessing a Wifi.
Then use:ifconfig
Then go to the wlan0 section, find your IP address. And remember this part: 192.168.X.X
Now fill in this command:nmap 192.168.X.0/24
Replace the “X” in the IP with the value I told you to remember.
It will proceed to sweep the network for any online hosts, then find port. You can fill in extra commands to make it stronger and scan better and more. Don’t worry, it’s only hard if you make it seem so.
The firewall evading scan technique:
Usually, hosts have firewalls to keep their ports to themselves. Even though that is the case, they do need to filter all kinds of packets. And you only need one single flaw to be discovered.
Firewall filtered ports will appear as “filtered” in the scan report. You need to select the right packet type to do the job. The packets range from TCP SYN (-sS), Connect()(-sT) to FIN(-sF), TCP Null(-sN) and more. The advanced packets do need root to work though. You can use:tsudo nmap -sF 192.168.X.0/24
For example, it scans the network via FIN packets so as to dodge firewall. If it succeeds, hooray. If it fails, try another packet type. If all fails, then sad for you.
You can learn all about Nmap at its homepage.
I hope you enjoy this tutorial. If you like, please share with your friend. And remember, stay ethical as we aren’t responsible for any of your malicious acts. Thank you and goodbye.
No comments:
Post a Comment
Note: Only a member of this blog may post a comment.